WireGuard is a simple and effective Virtual Private Network (VPN)
Understanding and implementing security software may be difficult. This may make it more difficult to utilize and install secure designs. WireGuard software, on the other hand, strives to bring us together with security solutions. Its goal is to provide a robust VPN connection between two PCs with only a few setup options. Indeed, its creator, Jason A. Donenfeld, has chosen to implement just a small number of cryptographic protocols, all of which are state-of-the-art, and to give the user a simple interface. Behind this abstraction, these options help obscure a lot of the VPN’s actual complexity. WireGuard also promises to give a high degree of performance in addition to its simplicity of configuration.
What is the purpose of a VPN?
We hear a lot about VPNs, but before we get one, let’s evaluate if we truly need one.
A Virtual Private Network (VPN) is a network architecture that allows encrypted and secure communication between two machines and, beyond these machines, between the two networks on each side of the machine before it becomes software. The tunnel that is encrypted The client-server approach is frequently used in this design, although not always.
The following are the most common usage cases:
- Professional use: a traveling professional will connect to their company’s VPN server after connecting to their hotel’s Wi-Fi. This will create an encrypted tunnel between his computer and the target server, via which all network data leaving the professional’s system will transit. The user in question may then be certain that no data flowing from his PC will be visible to someone scanning the network (DNS requests, unsecured web traffic, unencrypted electronic messages, etc.). As a result of the VPN connection, he may access not only his internal corporate network’s services and servers (internet server, business apps, messaging, and so on), but also his online surfing proxy.
- citizens or activists should use: We realize that once connectivity between your workstation and the VPN server is established, all of your network traffic is encrypted and sent to the servers. As a result, no further traffic inspection or modification is feasible between these two computers. A citizen of an authoritarian country, or, much worse, if the server is outside the reach of the state in issue, maybe confident that he will not be monitored or censored by official mass surveillance. Targeted assaults can still be made against your computer or smartphone, but we’re breaking out of the threat model that the VPN responds to in this scenario.
In a nutshell, the VPN enables you to:
- browse the internet with the assurance that your network communication between your system and your VPN server is neither visible nor changeable;
- secure access to your company’s network, and hence to services and resources that aren’t immediately accessible via the Internet;
- as well as the ability to conceal your true IP address This feature is not a complete risk insurance policy, but it is the first step toward more discretion.
Do you believe you’re interested in finding a simple and efficient VPN now that you’ve gathered all of this information? Yes?
So, let’s take a close look at WireGuard and see how it compares to OpenVPN.
WireGuard:
Before it is a tool, WireGuard is first and foremost a communication protocol. It was described and recorded transparently by its author.
The purpose is to make it easier to create implementations on a variety of platforms, in different languages, and with different architectural decisions than the reference version. For example, a developer may opt for a user-space-only solution rather than using a kernel module.
Let’s briefly go through some of WireGuard’s important features:
- It’s a level 3 (the same as IP) communication protocol.
- It transports data via UDP and has a tiny code size of roughly 3,700 lines.
- This software application was written in C, OpenBSD, and Go.
- Like a client-server solution, it may create peer-to-peer communication between the two workstations creating the VPN link.
- The notion of SSH keys (each computer has a set of private and public keys) is used to authenticate packets delivered by machines.
- The protocol is secretive: no packet that is not authenticated will obtain a response.
- It only implements a limited number of state-of-the-art cryptography algorithms. When these are found to be vulnerable as a result of an attack, they will be replaced with more secure equivalents.
- An essential aspect to note is that the protocol does not contain a phase of negotiation between the two computers on these methods. As a result, we eliminate any chance of a “downward negotiation” attack against less secure algorithms.
- Finally, WireGuard is based on a WireGuard-like network interface implementation. Suddenly, everything you can do on network interfaces (filtering, routing) is now possible on the VPN-only network interface supplied by WireGuard.
OpenVPN :
OpenVPN is a VPN protocol that was first introduced in 2001. It employs methods for establishing secure point-to-point or site-to-site connections. The protocol is open-source and includes features such as military-grade 256-bit AES encryption. It has a lot of security and control capabilities since it uses the OpenSSL encryption library and the TLS protocol. It was built with security in mind, has undergone independent auditing, and by default does not maintain logs. You may hide activities by switching ports using OpenVPN.
OpenVPN, on the other hand, has a few flaws. He utilizes between 400,000 and 600,000 lines of code on average. All of these lines of code increase the likelihood of discovering and exploiting system flaws. Although it is safe, it can cause performance problems. When a VPN connection is lost, several firms utilize kill switches to safeguard the user. Because of the long time, it takes for OpenVPN to reconnect, you should employ a kill switch to protect yourself. Encryption overflow is common with OpenVPN since it uses older technologies. Because it runs in userspace, it could be resource-intensive and slow down the system.
Let’s take a quick look at some of OpnVpn’s key features:
- It is a well-known open-source VPN tunneling protocol that has been approved by a significant number of security professionals and auditors.
- It makes use of the OpenSSL and TLS encryption libraries as the core cryptographic library.
- In terms of speed and security, the protocol performs admirably.
WireGuard VS OpenVPN :
PERFORMANCE :
WireGuard is far superior to the OpenVPN protocol.
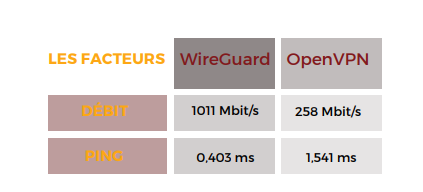
In terms of performance, OpenVPN isn’t the greatest option.
However, before multi-threaded processing became feasible, the difference was not significant. Today’s computers, on the other hand, are capable of multithreaded processing and better throughput.
Because OpenVPN is incorporated into the user space, its throughput and processing utilization are limited. As a result, it is unable to match the need for higher rates. WireGuard is a much simpler version of WireGuard that is embedded into the kernel space.
This allows it to run faster and make better use of modern processors’ multi-threading capabilities. As a result, in terms of ping and throughput, WireGuard can exceed OpenVPN. On WireGuard, benchmark testing (https://www.wireguard.com/performance/)
demonstrated how much OpenVPN lags:
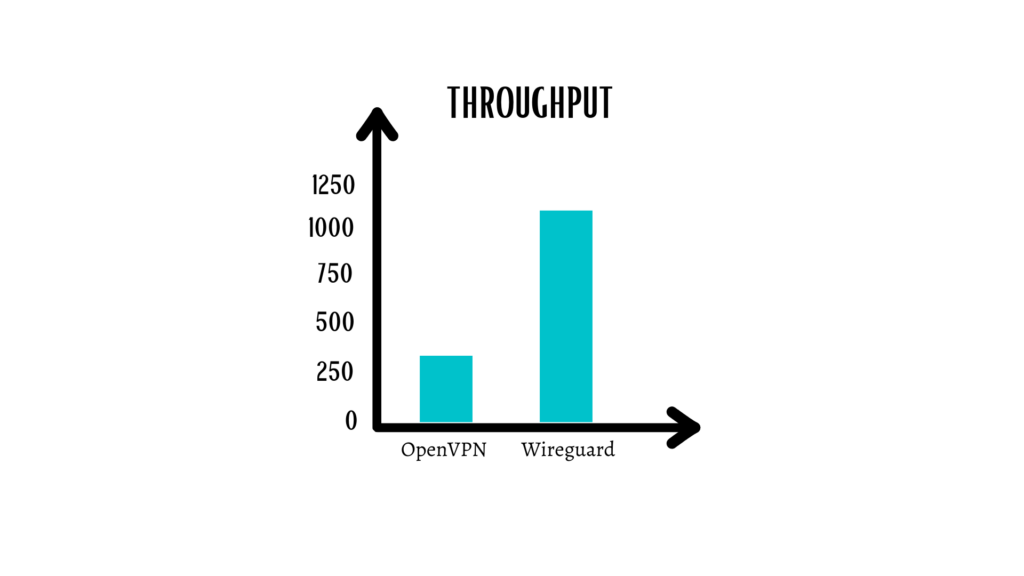
The distinction is unmistakable. WireGuard not only achieves over 100 percent throughput on a 1 Gbps connection, but it does it without using the CPU to its full potential. A CPU running OpenVPN, on the other hand, reaches a maximum speed of just 258 Mbps.
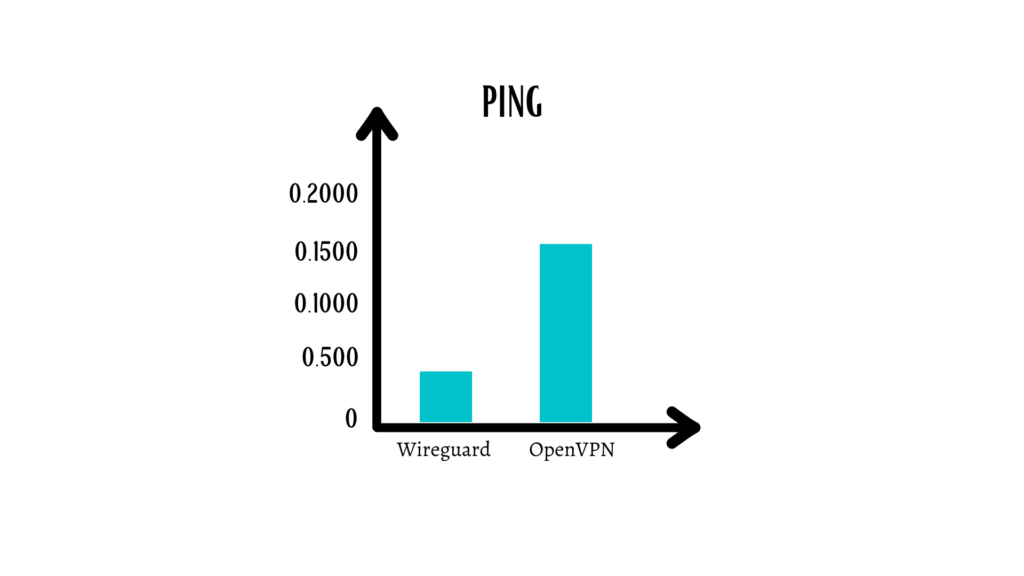
WireGuard’s ping time is less than half of OpenVPN’s. It’s worth noting that, despite its early stage of development, WireGuard already offers exceptional performance results.As a result, WireGuard puts OpenVPN to the test in terms of performance.
SECURITY :
WireGuard outperforms the OpenVPN protocol in terms of security.
When comparing the two protocols, we can see that OpenVPN employs safe encryption mechanisms. The OpenSSL package makes cryptographic bootstrapping extremely safe.
The use of RSA and AES for data and control channels further eliminates the possibility of brute force attacks.
OpenVPN employs a code HMAC authentication method for authentication. It employs AES and RSA for encryption.
WireGuard, on the other hand, employs a whole other set of encryption. ChaCha20, Curve25519, SipHash24, and BLAKE2s are among them. Comparing primers and cryptographic algorithms is not an easy task.
However, you can’t deny that the more contemporary an algorithm is, the safer it is. OpenVPN is a bit obsolete, despite the fact that it utilizes robust encryption. Furthermore, due to a higher code length, it provides a far broader attack surface than WireGuard.
WireGuard maintains its position as the more secure protocol of the two since it employs cryptographic methods that cryptographers do not trust.
USEFULNESS :
WireGuard is easier to set up manually than OpenVPN.
OpenVPN is made up of hundreds of thousands of lines of code. A developer’s work and time are required to change this code. Furthermore, it is incompatible with various systems, particularly on mobile phones (iOS users might know).
WireGuard, on the other hand, is designed on lean code that provides for outstanding usability and cross-platform interoperability. Despite having a simple interface, it is more powerful than any other protocol now in use.
Another characteristic that makes it more useful than WireGuard is that it is versioned.
OpenVPN is a certificate-based protocol, unlike WireGuard.
The encryption level of OpenVPN can be modified according to the user’s requirements. This necessitates the usage of security certificates for technical reasons. WireGuard, on the other hand, disregards cryptographic agility, focusing instead on versions particular to each sort of cryptographic protocol.
This lowers the expenses of establishing and reconnecting a VPN connection. Given that each WireGuard version will have its own encryption settings
Specifically, connecting to the servers will be twice as simple because the server will know what to expect from the client ahead of time.
As a result, WireGuard is simple to set up and configure for various devices, making it ideal for usage with OpenVPN.
AUDITABILITY :
The OpenVPN protocol is easily auditable by WireGuard.
Because OpenVPN is the most frequently inspected VPN protocol, this is the most difficult attribute to compare. Because of the several levels of auditing that OpenVPN has undergone, it has gained the trust of security professionals and cryptographers.
It’s been 17 years since the protocol was created, giving software experts plenty of time to evaluate, validate, and audit it. The fact that it is open source has made auditing much easier.
Despite being the most audited tunneling technology, OpenVPN is also the most difficult due to the large number of lines of code it includes.
To audit correctly code as huge as OpenVPN, it needs an entire team.
WireGuard, on the other hand, has not yet been subjected to the same rigorous audits, although this is partly owing to its youth. WireGuard is substantially more verifiable than OpenVPN because of its much simpler code.
The code is so little that it can only be audited independently by one person who knows how to do it. It means that, after the release of its first stable version, WireGuard will become the most commonly audited protocol.
Better audits also result in fewer defects, improved security, and reduced susceptibility.
Despite the fact that OpenVPN is a well-audited protocol, maintaining this status after WireGuard is introduced will be extremely challenging. As a result, WireGuard takes the cake when it comes to audits, which is much superior in its case compared to OpenVPN.
GRAPHIC INTERFACES FOR WIREGUARD SERVER
WG-UI :
WG-UI is a WireGuard client interface that is exceedingly basic. Embark Studios, a game development firm headquartered in Sweden, was responsible for the initial development of this project. The engineers have put a lot of attention into this project. There is extensive build documentation, and it can also be cross-compiled into a few different architectures.
The user interface is clean and easy, and it allows you to manage your peers with simple QR codes. This is more of a self-service site that enables end-users to control their own endpoints.
You can, however, manage client configurations.
In terms of peer setup, there’s also not much you can do. The only extra field is a nickname value for each peer, which is produced automatically. More server-side functionality can be found in the following project.
WIREGUARD-UI :
It gives you more freedom and control over the WireGuard server itself. The WireGuard hub as well as client settings are managed by this project.
From a single dashboard, you can add custom scripts, alter server endpoint settings, and manage clients. Wireguard-ui is comparable to wg-ui in terms of peer management, but it includes a few extra features such as an email address, timestamps, and the option to deactivate clients.
You may quickly start up the project with Docker and import an existing server configuration, or you can build the Go binary from scratch.
SUBSPACE :
In the same way that the WG-UI project focuses on offering a self-service portal for maintaining peer setups, Subspace does as well. The difference is in the granularity with which Subspace allows you to create and manage these setups. You may categorize peers into different groups, utilize an SSO provider to log in users and create profiles with several setups. When it comes to clients and authentication, the Subspace project has a lot of power.
Subspace has a number of drawbacks, one of which is that it can be difficult to set up and utilize. Subspace, in comparison to the other projects described, needs a significant number of stages to be properly executed. You’ll need to set up a Linux instance, perform a few commands, and double-check that your domain and certificate requirements are valid.
Unfortunately, you won’t be able to simply test this project using docker-compose up.
WG-MANAGER :
WG-MANAGER is a simple and versatile user interface that lets you control both the peers and the server. In this project, you may have more precise control over both the server and the peers. Directly from the administration interface, the controls enable you to stop, start, and inspect raw configurations.
Like previous projects, you may quickly add and remove peers, as well as apply unique nicknames to each peer entry. The peer layout is a little prettier, and it’s really useful for figuring out who’s connected, sending more traffic, and so on. The quantity of information you can display in the dashboard grid system is astounding, even though the user interface may be a little clumsy at times.
wg-manager achieves an excellent combination of form and function.
There are numerous options for configuring new WireGuard servers or importing an existing configuration into the project.
MISTBORN :
Although Mistborn does not have a specific WireGuard user interface, it does provide a set of services that includes a rudimentary WireGuard administration interface. Mistborn is a project with the goal of providing a completely customized set of private cloud services with an integrated firewall. This is meant to sit in the center of your existing network and provide you control over all traffic, not just VPN traffic.
WIREGUARD EASY
The simplest way to manage WireGuard VPN is via the web interface.
Characteristics :
- WireGuard Plus web user interface in one package.
- It’s simple to set up and utilize.
- Clients can be listed, created, modified, deleted, activated, and deactivated.
- View the QR code of a customer.
- The configuration file for a client can be downloaded.
- Customers who have logged in statistics.
Condition:
- A host having a WireGuard-compatible kernel (all contemporary cores).
- Docker is installed on a host.
Configuration du serveur VPN
WireGuard will be installed first on our server. It should be noted that all changes to the system and WireGuard settings will want administrator privileges on your machine.
#apt-get install wireguard wireguard-tools net-tools linux-headers-`uname -r`The WireGuard server’s public and private keys are then generated
As previously stated, private and public keys are used to authenticate the packets transmitted by the computer. As a result, it is essential to produce, respectively, privatekey and publickey files.
#cd /etc/wireguard/
#umask 077; wg genkey | tee privatekey | wg pubkey > publickeyGenerate the configuration file We are going to create the /etc/wireguard/wg0.conf configuration file and finish it with the first part of the configuration from the server after having retrieved the name of your network card bearing your public IP address using the ifconfig command.
[Interface]
Address = The_VPN_server_private_IP_address
ListenPort = 51820
PrivateKey = Copy_The_Key_Here
PostUp = iptables -A FORWARD -i wg0 -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE;
ip6tables -A FORWARD -i wg0 -j ACCEPT; ip6tables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown = iptables -D FORWARD -i wg0 -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE;
ip6tables -D FORWARD -i wg0 -j ACCEPT; ip6tables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
SaveConfig = true- Address: provide the VPN server’s private IP address.
- SaveConfig: The current state of the interface must be used to save the configuration during the shutdown.
- PrivateKey: The VPN server’s private key, which is stored in the server’s /etc/wireguard/server private.key file.
- PublicKey: The VPN client’s public key, which is stored on the client computer in the /etc/wireguard/client public.key file.
- ListenPort: WireGuard VPN server will listen on UDP port 51194. Otherwise, the default port is 51820.
- PostUp and PostDown: allows you to place orders when connecting and disconnecting a peer. Useful in the case of connection sharing via VPN.
then we activate the VPN via the wg-quick up wg0 and wg show commands
# sudo wg-quick up wg0
#sudo wg showWe’ll now set up the WireGuard VPN client.
After activating the wireguard repositories, we use apt-get to install it.
#sudo add-apt-repository ppa:wireguard/wireguard
#sudo apt-get install wireguard resolvconfAfter that, we generate the client’s private and public keys:
cd /etc/wireguard/
umask 077; wg genkey | tee privatekey | wg pubkey > publickeyThen create the /etc/wireguard/wg0.conf file with the configuration that goes well:
[Interface]
Address = The_VPN_server_private_IP_address
DNS = 9.9.9.9
PrivateKey = COPY_THE_CLIENT'S_PRIVATE_KEY_HERE
[Peer]
PublicKey = COPY_THE_SERVER'S_PUBLIC_KEY_HERE
AllowedIps = 0.0.0.0/0
Endpoint = COPY_THE_SERVER'S_IP_ADDRESS_HERE:51820The client’s private key is stored on the laptop in the /etc/wireguard/privatekey file.
The public key for the server can be found in the /etc/wireguard /publickey file on the server.
a key point: the value 0.0.0.0/0 in the AllowedIPs variable indicates that all outbound traffic from the client will be routed through the VPN tunnel.
Enabling and disabling the VPN connection :
Simply enter the identical command on both the server and client sides;
#sudo wg-quick up wg0Similarly, you can stop the VPN connection.
#sudo wg-quick down wg0WireGuard is now set up on both the server and the first client. All you have to do is utilize this VPN to stay safe while traveling while also benefiting from its high level of performance.
Zen Networks is a leading provider of advanced IT solutions, specializing in log monitoring, automation and DevOps.
Our expert team offers a wide range of services, including IT monitoring, cloud services, agile solutions, and automation. We are also well-versed in the installation and implementation of Elasticsearch, Logstask, and Kibana on Docker.
By leveraging our extensive domain expertise and innovative technologies, we empower our clients to optimize their IT infrastructure and achieve operational excellence. Our solutions are designed to help organizations of all sizes to streamline their processes, improve efficiency, and reduce costs.
We invite you to take advantage of our complimentary consultation and quote service to learn more about how we can help your organization to achieve its IT goals. Contact us now to schedule your consultation and discover the benefits of working with Zen Networks.
Author





