What Is Security Information and Event Management (SIEM)?
What Is Security Information and Event Management (SIEM)?
Security information and event management (SIEM) is a cybersecurity system that gives you a unified, simplified view of your data, understanding of security activities, and operational capabilities so you can detect, look into, and address security risks efficiently.
That combines security event management (SEM) and security information management (SIM), two legacy systems, into a single security management solution. Also included in modern SIEM SOAR, which automates threat response, and UEBA, which identifies risks based on abnormal activities. Together, these features enable quicker identification and reaction to security events or incidents in an IT system.
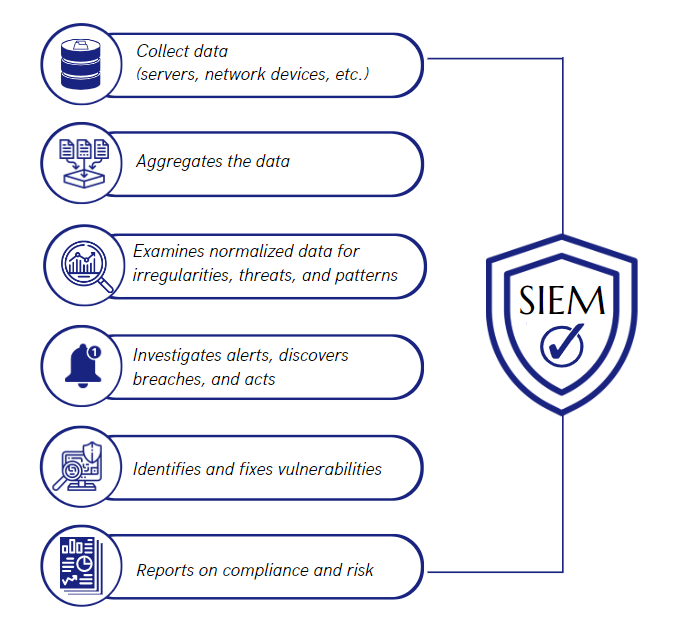
SIEM technology collects event log data from many sources, analyzes it in real-time to spot activity that differs from the usual, and then takes the necessary action. As a result, SIEM provides enterprises with visibility into network activity so they can respond quickly to potential cyberattacks and comply with regulatory obligations.
How does SIEM work?
SIEM software collects and organizes log data captured throughout the whole IT infrastructure, from network and security tools like firewalls and antivirus software to cloud services and applications. Then, SIEM locates, classifies, and examines occurrences and events.
In the end, a SIEM analytics provides numerous crucial business and management units with real-time alerts, dashboards, and reports. In addition, unsupervised machine learning is used by contemporary SIEMs to provide anomaly detection (User and Entity Behavior Analytics) on the gathered log data.
Among the data sources are :
Network devices: Routers, switches, bridges, wireless access points, modems, hubs
Servers: Web, proxy, mail, FTP
Security devices: IDS/IPS, firewalls, antivirus software, content filter devices
Applications: Any program run on the aforementioned hardware
Cloud and SaaS solutions: Non-premises hosted software and services.
The Threat Hunting and Detection
The key to managing the strategic, tactical, and operational aspects of threat hunting—none of which can be neglected in the threat landscape of today—is the usage of an intelligent SIEM. To increase visibility into potential threats and detect vulnerabilities and to boost security posture as the organization scales, effective integration of SIEM as the focal point working with threat investigation tools is essential.
Reduced Response Time
In order to enable quick identification of events involving interactions with dubious or malicious IP addresses, SIEM can make use of the capability of global threat intelligence. Rapid identification of attack vectors and previous interactions speeds up the process of dealing with environmental risks.
Real-time visibility
Data production by organizations is at an all-time high. SIEM technologies must ingest data from all sources, including cloud and on-premises, to keep up with the rise in data in order to efficiently monitor, detect, and react to potential risks.
Analysts will have greater visibility into activities and be more proficient at identifying and countering threats the more data an organization can offer to its SIEM software.
Incident response
Beyond the fundamental security monitoring and reporting, modern SIEMs offer more. They give analysts the clarity they need to accelerate decision-making and response times, creative data visualization, and wise business context to help them better understand and act on the data’s guidance. Teams are better able to manage events and enhance their capabilities as incident response grows more sophisticated.
Reporting on and Evaluating Compliance
For many companies, compliance auditing and reporting is a crucial yet difficult duty. SIEM systems greatly reduce the amount of resources required to manage this process by providing real-time audits and on-demand reporting of regulatory compliance whenever necessary.
Choosing a SIEM Solution
There are many options available for you to think about when the time comes to make a choice. The most important qualities to consider in a SIEM as you compare tools are as follows:
- Real-time monitoring: Attacks happen swiftly, and the more you delay responding to them, the more harm they cause. Your SIEM should give you a real-time, aerial picture of everything going on in your network, including user, device, and application-related activity as well as any other activity that isn’t particularly associated with an identity. You require monitoring tools that can be used with any on-site, cloud-based, or hybrid data set.
- Incident response: Above all, an analytics-driven SIEM must have auto-response capabilities that can stop cyberattacks in the middle of them. Additionally, it should give you the option to recognize important occurrences and their state, describe their seriousness, initiate a remediation procedure, and provide an audit of the complete procedure leading up to that incident.
- User monitoring: Some threats could be internal, either because people actually pose a threat or because their actions expose the company to threats from the outside. Your SIEM technology should, at the very least, include user monitoring that examines authentication and access data, establishes user context, and issues alerts regarding suspicious behavior and transgressions of corporate and regulatory regulations.
- Threat intelligence: Your SIEM should assist you in locating significant external threats, such as recognized zero-day exploits and sophisticated persistent threats. Threat intelligence gives you the capacity to not only spot unusual activity but also to spot security flaws before they are exploited, as well as to plan responses and remediations.
- Scalability: Make sure your chosen SIEM can accommodate your needs both now and in the future, especially as your organization develops and your IT infrastructure evolves.
The cybersecurity of an organization should include SIEM. In order to streamline security operations, SIEM provides security teams with a central location to gather, combine, and analyze large amounts of data from across a business. Additionally, it offers operational features including dashboards that rank threat activity and compliance reporting and incident management. Therefore, SIEM offers businesses network activity visibility so they can react fast to suspected assaults.
Zen Networks is a leading provider of advanced IT solutions, specializing in log monitoring, automation and DevOps.
Our expert team offers a wide range of services, including IT monitoring, cloud services, agile solutions, and automation. We are also well-versed in the installation and implementation of Elasticsearch, Logstask, and Kibana on Docker.
By leveraging our extensive domain expertise and innovative technologies, we empower our clients to optimize their IT infrastructure and achieve operational excellence. Our solutions are designed to help organizations of all sizes to streamline their processes, improve efficiency, and reduce costs.
We invite you to take advantage of our complimentary consultation and quote service to learn more about how we can help your organization to achieve its IT goals. Contact us now to schedule your consultation and discover the benefits of working with Zen Networks.
Author





